According to Statista, the global mobile health market reached $172 billion dollars in 2024 and will keep growing to $258 billion by 2029. Such growth of mobile healthcare (mHealth) is driven by technological advances – wearable devices, telemedicine – and the demand for remote care and more personalized services. This rapid growth comes with a heavy responsibility: protect sensitive patient data and maintain its privacy.
At the center of this obligation is HIPAA – the Health Insurance Portability and Accountability Act. For any business developing a healthcare app, HIPAA compliance is a must requirement that helps ensure strong data protection, avoid costly penalties, and build long-term trust with users and partners.
In this guide, we’ll walk you through everything about “how to make an app HIPAA-compliant”, including the law explanation, detailed development process and best practices to ensure your app meets all regulatory rules.
What is HIPAA?
HIPAA, or the Health Insurance Portability and Accountability Act, is a federal law established in 1996 to protect the privacy and security of personal health information in the U.S. Simply put, HIPAA sets out strict rules on how and who can access, manage, transmit, and store protected health information (PHI) to ensure its confidentiality and security.
The law also outlines penalties for non-compliance with HIPAA rules. HIPAA is structured around key standards that uphold the confidentiality, integrity, and security of health information, which ultimately strengthens the healthcare system. They include:
- Privacy rule
- Security Rule
- Enforcement Rule
- Breach Notification Rule
- Omnibus Rule
Let’s consider each of them closely below.
Primary rules of HIPAA law
The primary rules of HIPAA law include:
Privacy Rule (2003): it ensures the protection and privacy of all health information and grants individuals rights over their data. It also regulates how covered entities (e.g., healthcare providers) and business associates may use and disclose PHI.
Security Rule (2005): set standards for protecting electronic health information (ePHI) by covering three types of safeguards:
- Administrative: policies and procedures to manage security measures, including employee training, risk assessments, and contingency plans.
- Physical: measures to protect electronic systems, equipment, and data from physical threats, unauthorized access, or data breaches – such as facility access controls, workstation security, and device management.
- Technical: measures to control and protect PHI access – like access controls, encryption, audit controls, multi-factor authentication (MFA) and secure communication channels.
Unlike the Privacy Rule, which covers all PHI, it is used only for ePHI to ensure its confidentiality, integrity, and security both in storage and during data transmission.
Enforcement Rule (2006): procedures for investigations, penalties, and non-compliance related to HIPAA. Depending on the severity and circumstances of the breach, fines for HIPAA violations can range from $100 to $50,000\violation.
Breach Notification Rule (2009): requires covered entities (organizations) and business associates to notify individuals\patients, of the Department of Health and Human Services (HHS) in the event of a breach due to unsecured PHI. Notification must be provided within 60 days of discovering the breach.
Omnibus Rule (2013): it strengthens all HIPAA rules and expands the responsibilities of businesses that handle healthcare data, including Business Associates (BAs) and their subcontractors.
Who must comply with HIPAA?
HIPAA also provides information about who is strictly required to comply with its regulations. Compliance is mandatory for two key groups of organizations:
- Covered Entities: organizations that are directly involved in the creation, use, or transmission of protected health information (PHI). Examples include healthcare providers (doctors, hospitals), health plans (health insurance companies), and healthcare clearinghouses.
- Business Associates: individuals or organizations that perform services involving PHI on behalf of covered entities, such as IT services, billing companies, or third-party vendors.
Business associates must sign a Business Associate Agreement (BAA) to confirm their compliance with HIPAA rules. Business Associate Agreement (BAA) is an agreement that sets the specific responsibilities and obligations that each party must fulfill to comply with HIPAA.
For example, a small doctor’s office (covered entity) hires a cloud storage company (business associate) to store patient records. Both must sign a BAA, follow HIPAA rules, and regularly review and update the agreement as needed. In some cases, subcontractors who handle PHI must meet HIPAA as well. This ensures that PHI is protected, regardless of who processes it.
PHI, ePHI and CHI: what is the difference?
PHI, ePHI and CHI are widely used terms in healthcare but they differ in scope and regulatory coverage. Recognizing the differences between these terms is essential for ensuring appropriate data protection in healthcare and beyond.
Protected Health Information or PHI: is any information related to an individual’s health that is collected and maintained by a covered entity (healthcare organizations) under the HIPAA law. It specifically includes data that can be used to identify an individual, for example:
- Name
- Address
- Email address
- Social Security number
- Medical record numbers
- Insurance info
- Account numbers
- Medical info
- Device identifiers and serial numbers
- Certificate/license number
- Web URLs
- Biometric data
Examples of PHI:
- Medical records
- Insurance claim data
- Diagnostic test results
PHI is strictly regulated by HIPAA to ensure its privacy and security.
Electronic Protected Health Information or ePHI: is a type of PHI that is stored, transmitted, or accessed electronically. In other words, it’s the digital version of Protected Health Information (PHI) that is protected by the same Privacy and Security rules under HIPAA.
Examples of ePHI:
- Electronic medical records (EMRs)
- Electronic health records (EHRs)
- Billing and insurance data stored in digital form
- Test results, prescriptions, and diagnoses transmitted electronically
Because ePHI is stored and transmitted digitally, it requires additional security measures like encryption, secure networks, to protect it from unauthorized access, breaches, or cyberthreats and to comply with HIPAA’s Security Rule.
Consumer Health Information or CHI: is a broader term for any health-related information that is considered private or sensitive. Unlike PHI and ePHI, it’s not always covered by HIPAA. It can include health data shared in non-healthcare settings, like wellness applications.
Examples of CHI:
- Fitness tracker data
- Non-identifiable medical data
- Health-related data disclosed outside of healthcare systems
Although CHI may not always be regulated by HIPAA, it could still fall under other privacy laws or standards, like GDPR.
Thus, PHI and eHPI are specific legal terms in the healthcare industry with strict HIPAA rules, while CHI is a more general term related to confidential health-related information, which might not always fall under the same regulatory protections.
When does an application need to be HIPAA-compliant?
Once we’ve covered what HIPAA is, its primary rules, and who must adhere to them, the common question may arise: “when exactly does an application need to comply with HIPAA?” The answer is clear – an application must comply with HIPAA if it:
- Stores, processes, transmits, or shares PHI
- Works with or on behalf of healthcare providers or other covered entities
- Involves third parties that handle PHI
- Provides healthcare-related services involving PHI
In short, if an application interacts with PHI in any way, it must follow HIPAA regulations to protect the privacy and security of that data.
Importance of HIPAA compliance
HIPAA strikes a balance between efficient healthcare delivery and the protection of patient privacy and data security. Thus, it benefits patients, healthcare providers, and startups alike in the following ways:
For patients:
- Protect privacy: it ensures that patients’ medical data, diagnoses, and treatments remain confidential and secure. HIPAA limits who can access or share a patient’s health data, giving them control over their information.
- Reduce security risks: by requiring strong security measures – like encryption, access controls, and audits – HIPAA reduces the risk of data breaches, unauthorized access, or cyber threats.
- Control over data: patients are granted access to their medical records and know how they are used, ensuring they are informed and engaged in their care.
- Improved quality of care: secure information sharing between authorized providers, leading to better coordination and personalized treatment.
For hospitals:
- Avoid reputation damage: non-compliance with HIPAA regulations can result in severe fines, legal issues, and reputation damage. Hospitals can avoid these risks by meeting HIPAA regulations.
- Streamlines operations: by implementing standardized processes, hospitals can improve data sharing, billing, and communication within the healthcare system.
- Reduce risk of cyberthreats: HIPAA regulations require healthcare providers to set and comply with security measures to protect electronic health information, reducing the risk of data breaches and cyberattacks.
- Improve patient trust: patients are more likely to trust healthcare providers if they trust that their data will remain confidential and secure. HIPAA fosters transparency between providers and patients, leading to stronger relationships.
- Supports interoperability: compliance ensures that hospitals securely share patient information with other providers, improving care coordination.
For startup owners:
- Build trust with investors and partners: investors and business partners prefer to work with startups compliant with regulations such as HIPAA as it demonstrates expertise and builds trust.
- Reduce legal and financial risks: by complying with HIPAA, startups will avoid hefty fines, lawsuits, and potential reputational damage, protecting their business and future growth.
- Enhance security: HIPAA compliance helps implement necessary security measures for protecting health data, ensuring you have the right infrastructure in place to prevent any problems.
- Long-term growth: HIPAA compliance lays a solid foundation for future growth, allowing a startup to scale without worrying about regulatory issues later on.
To sum up, HIPAA regulations help reduce security and financial risks and build trust with partners and patients, ensuring sustainable business growth in the healthcare industry.
How do you make the application HIPAA-compliant?
When it comes to answer the “how to build a HIPAA-compliant app?” question, you must follow all the rules – Privacy, Security, Enforcement, Breach Notification and Omnibus – set by HIPAA. As your app will handle electronically protected health information (ePHI), you must implement three key safeguards outlined in the Security Rule: administrative, physical, and technical – let’s talk about them below.
Technical safeguards:
- Encrypt all patient data (both storage and transmission) using algorithms like AES-256;
- Use strong authentication mechanisms, like biometric recognition or multi-factor authentication;
- Use secure coding practice like input validation;
- Use monitoring and logging systems;
- Regularly update your mobile app.
Physical safeguards:
- Implement access controls;
- Regularly back up patient data;
- Check your app supports encryption and protection for mobile devices;
- Train your staff about physical security;
- Ensure secure disposal of outdated devices with healthcare data;
- Update physical security measures.
Administrative safeguards:
- Develop and implement security policies for dealing with PHI including rules for the use of mobile devices.
- Develop procedures for responding to security incidents;
- Provide regular training to employees on HIPAA regulations and best practices;
- Assign a HIPAA Compliance Officer to monitor compliance with security measures and conduct regular risk assessments;
- Conduct regular audits and risk assessments.
To help you not miss anything important, we provide a step-by-step HIPAA app development process.
HIPAA compliance application development process: key steps
Here are the key steps toward HIPAA-compliant app development :
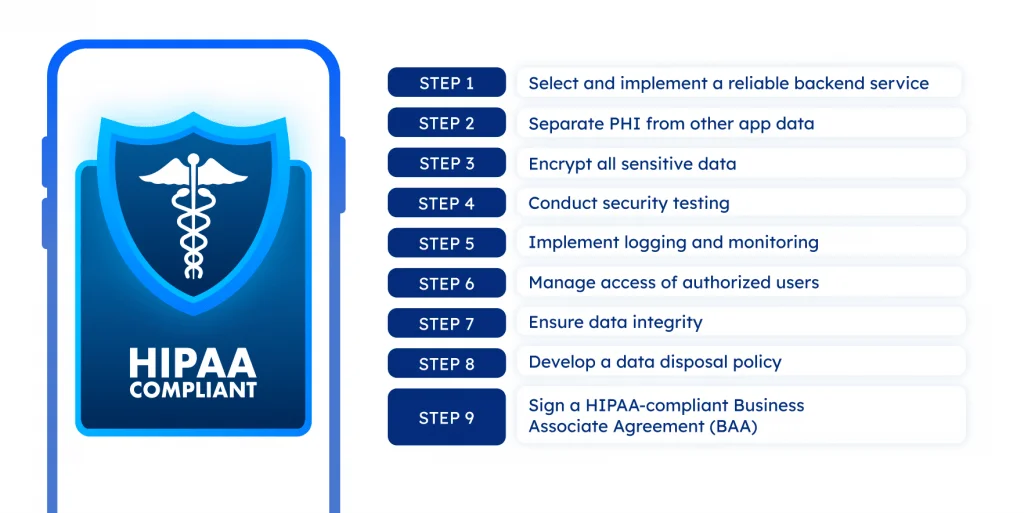
Step 1: Select and implement a reliable a backend service
You can start by choosing the most appropriate backend provider that meets HIPAA standards, like AWS, Microsoft Azure, Google, or IBM Cloud. Each provider offers HIPAA-eligible services, including relevant services and data centers. For example, AWS provides EC2 for computing, S3 for storage, and RDS for databases.
When selecting a provider, verify that their infrastructure meets HIPAA security and privacy rules, including built-in encryption, role-based access control, and backup requirements. You can verify a provider’s HIPAA compliance by reviewing their business associate agreement (BAA) to ensure they follow the law.
Step 2: Separate PHI from other app data
You need to separate protected health information (PHI) from other data types. For that, start by categorizing all the data that your app processes – which data is PHI and which is not. PHI includes health-related info that can be tied to an individual, like medical records, diagnoses, treatment, and payment details. Non-sensitive data can consist of user preferences, analytics, or marketing data.
Next, store PHI and non-PHI data separately – in databases or storage services. This will help you ensure the security and proper handling of sensitive health data.
Step 3: Encrypt all sensitive data
Under HIPAA, organizations handling ePHI must implement proper security measures, and encryption is one of the most effective methods to protect data both at rest and in transit. It prevents data breaches and unauthorized access to the data. So, during this stage, you’ll need to:
- Encrypt data at rest: ensure that all PHI stored in databases, file systems, or cloud storage is encrypted using strong encryption standards, such as AES-256.
- Encrypt data in transit: use Transport Layer Security (TLS) 1.2 or higher to encrypt PHI during data transmission over networks. This will ensure that data is protected while being sent between the app and servers or between different components of a system.
Don’t use older protocols like SSL or TLS 1.0/1.1, as they are more vulnerable to attacks. Also, check that any third-party services your app uses follow secure protocols for encrypting data.
Step 4: Conduct security testing
Security testing is a crucial part of app development, especially when ensuring HIPAA compliance. Unlike standard QA, it involves more advanced procedures such as penetration testing, vulnerability scanning, and code reviews. These activities help detect and fix potential security flaws early on, protect sensitive data, and prevent breaches.
You can delegate this task to experienced third-party vendors, like SoftTeco, that specialize in security testing. We use automated tools such as Nessus, Qualys, or OWASP ZAP, which focus on HIPAA compliance specifically. These tools scan your application for vulnerabilities and provide reports on areas needing further attention.
Note: your developers can use tools, such as the HIPAA Security Risk Assessment Tool and HIPAA Audit Protocol – offered by the Office for Civil Rights (OCR) – which provide clear steps for assessing and analyzing data security.
Step 5: Implement logging and monitoring
HIPAA requires tracking and monitoring all access to PHI to keep data secure. This is needed to detect potential threats and suspicious activities in real-time. How to do it:
You need to log every interaction with PHI, including who accessed it, when, and what they did. Store these logs in a centralized location with encryption (both in transit and at rest) to simplify monitoring and analysis. You can use real-time monitoring tools to catch suspicious activity, like failed login attempts.
Also, you need to set up automated alerts to notify your team if something unusual occurs. Define an incident response plan to handle detected breaches promptly. You must conduct regular audits and review logs to find and fix security gaps proactively.
Step 6: Manage access of authorized users
When developing a healthcare app, controlling data access is crucial. To do this, you need to set up identity and access management policies (IAM). It’s a system that includes all processes, tools, and policies to control access to data. It ensures that only authorized users can view, edit, or delete medical information – with permissions granted based on their roles.
Key measures include:
- Role-based access control (RBAC): limit access based on user roles.
- Multi-factor authentication (MFA): add extra security by verifying user identity.
- Real-time access control: monitor and control access as it happens.
- Regular access reviews: check and update user permissions.
You can also use tools like Auth0 or Okta to help you configure IAM systems to meet HIPAA requirements. By managing user access carefully, you can minimize security risks.
Step 7: Ensure data integrity
Ensuring data integrity guarantees that health information remains accurate, complete, and unaltered over time. It’s vital in healthcare, where even a small data error can affect diagnosis, treatment, or compliance. To maintain data integrity within your app, you must implement measures like:
- Data validation: verify that all input data is accurate, consistent, and meets predefined formats or rules.
- Error detection: use checksum or hash algorithms to identify and prevent data loss during storage or transmission.
- Maintain audit logs: maintain detailed logs of data access and changes to detect any unauthorized alterations.
- Real-time monitoring: deploy monitoring tools to detect and respond to problems immediately.
With these measures, you can protect sensitive data from accidental errors and security threats and meet compliance requirements.
Step 8: Develop a data disposal policy
Under HIPAA, you need a clear data disposal policy that outlines the processes and methods for securely deleting or destroying PHI. Your policy should specify how long different types of PHI must be kept based on legal and business needs. For example, medical records may need to be stored longer than administrative docs.
Once PHIs have reached the end of their retention period, you must permanently remove them from your systems. For this, use secure destruction methods, like cryptographic erasure (which makes data unreadable) or physically destroying storage media (such as shredding hard drives).
After the PHI is securely disposed of, document the destruction process to prove compliance. You must regularly review and update your disposal practices to ensure they meet HIPAA standards and keep PHI secure over time.
Step 9: Sign a HIPAA-compliant Business Associate Agreement (BAA)
The final step to ensure HIPAA compliance for your app is to sign a Business Associate Agreement (BAA) with any third-party vendors or service providers who handle, process, or store PHI on your behalf.
A BAA is a legal contract between a healthcare provider (or covered entity) and a third-party vendor (business associate) that outlines how both parties will protect and properly use PHI, following HIPAA rules. If your app works with PHI and uses vendors (cloud hosting, analytics, payment processors), you must have a signed BAA with them.
Key points that must be in a HIPAA-compliant BAA are:
- Permitted uses and disclosures of PHI: limits how the vendor can use PHI.
- Data safeguards: include administrative, physical, and technical safeguards.
- Breach notification: obligates the BA to report breaches within 60 days.
- Subcontractor compliance: ensures any subcontractors (sub-BAs) also follow HIPAA.
- Audit and inspection rights: allows the covered entity to check the vendor’s compliance.
- HIPAA compliance: confirms the vendor will follow all HIPAA rules, including privacy, security, and breach notification requirements.
- Data return/destruction: specifies how PHI is handled when the contract ends.
By signing a BAA, you safeguard PHI and make sure all parties comply with HIPAA regulations as well.
As you can see, developing a HIPAA-compliant app requires a structured approach but there is one more critical factor to pay attention to – selecting the right features.
Key features of a HIPAA-compliant application
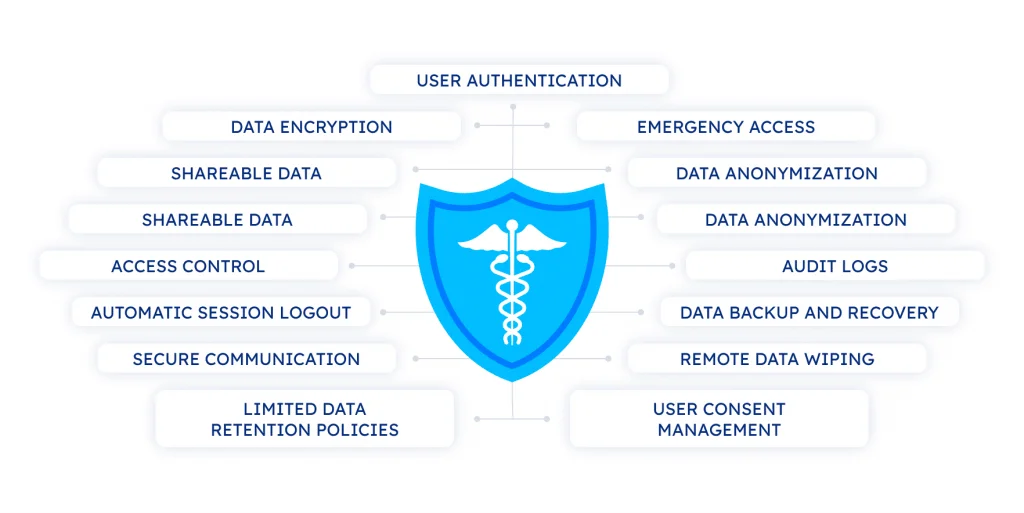
Even though any software is unique, and healthcare is no exception, there is a basic set of features every healthcare application must have to meet HIPAA law. They include:
User authentication
The feature requires users to log in with a unique account using strong credentials – complex passwords, biometrics (fingerprint, facial recognition), or multi-factor authentication. It prevents unauthorized access to protected health information (PHI).
Data encryption
Encryption is a must to protect sensitive healthcare information, as it does so at rest and in transit using strong algorithms like AES-256 and TLS. It prevents unauthorized access in case of data breaches or interception.
Emergency access
The feature instantly makes critical patient data available in urgent situations, like medical emergencies or system failures. It balances security and the need to respond quickly in critical situations without violating HIPAA.
Shareable data
Standardized data formats like HL7 (Health Level Seven) and FHIR (Fast Healthcare Interoperability Resources) are used for secure data exchange for interoperability between different systems. This ensures real-time access to data and better collaboration between healthcare settings.
Data anonymization
This removes or replaces personally identifiable information (PII) in datasets to prevent individuals from being identified. It enables you to analyze and research datasets when needed while still complying with privacy regulations.
Access control
The feature restricts access to data based on roles, in combination with multi-factor authentication (MFA) and the principle of minimum privilege. This ensures that only authorized users can access and modify PHI.
Audit logs
Audit logs, or audit trails, track and record all user interactions with PHI, including access, modifications, and data transfers. The feature helps ensure compliance, detect suspicious activity in real-time, and enhance security by providing regular monitoring and detailed analysis.
Automatic session logout
It automatically logs users out of the app after a period of inactivity to prevent unauthorized access from unattended devices. It enhances security by requiring reauthentication for continued access.
Data backup and recovery
The feature regularly backs up PHI and ensures quick recovery in case of system failures, cyberattacks, data loss, or other unexpected issues. This allows you to maintain data integrity and availability of your health data at all times – a key requirement of HIPAA.
Secure communication
The feature encrypts all communication channels to transmit data between providers, systems, and patients. It prevents eavesdropping and tampering with PHI during communication and ensures protected data in real time.
Remote data wiping
The feature allows you to remotely wipe data from a device if lost or stolen. It helps prevent possible data breaches and keeps PHI from being compromised.
Limited data retention policies
The feature automatically deletes or archives data that is no longer needed after a set period of time. It reduces the risk of exposing outdated or unnecessary data by supporting the HIPAA principle of minimum necessary use.
User consent management
The feature allows patients to give, withdraw, and manage consent to share data and make treatment decisions. It places control in the hands of the patient and ensures that all data use is legally authorized and properly documented.
Technology stack for HIPAA compliance app development
When it comes to selecting a technology stack for an app with HIPAA in mind, you need to balance security, scalability, and compliance requirements. A well-chosen tech stack will help you protect sensitive patient data, speed up development, simplify audits, and reduce the risk of costly violations. Here is a recommended tech stack for building a HIPAA-compliant app:
- Frontend: React, Angular, Vue.js, React Native, Swift, Kotlin
- Backend: Node.js, Python (Django/Flask), Java, .NET., Ruby
- Databases: MySQL, PostgreSQL, MongoDB, Amazon RDS or Google Cloud SQL, Oracle DB
- Cloud services: AWS, Microsoft Azure, Google Cloud
- Encryption: AES-256, TLS 1.2/1.3.
- Authentication: OAuth 2.0, OpenID Connect, Multi-Factor Authentication (MFA)
- Monitoring & Auditing: Splunk, ELK Stack, Datadog
- API Management: AWS API Gateway, Apigee, AWS, RESTful API, GraphQL, OAuth 2.0
- Compliance tools: HIPAA secure messaging, compliance tracking tools
Note: Use cloud providers that offer HIPAA-compliant services and support. They typically offer specialized services, such as secure storage, managed databases, and compliance monitoring tools. With it, your development team can focus on delivering expected functionality instead of reinventing compliance from scratch.
Always sign a Business Associate Agreement (BAA) with your cloud provider and vendors, even if they seem trustworthy to you. It’s not a useful tip – it’s one of the requirements of HIPAA.
Best practices to achieve HIPAA compliance
As we said above, developing a HIPAA-compliant software is a complex process that involves a lot of steps and aspects (technical, physical, and administrative) to keep in mind. Here are best practices that will help you ensure HIPAA compliance.
Partner with experts
Achieving HIPAA compliance requires a deep understanding of legal and technical requirements. Partnering with experts in healthcare law, IT security, and HIPAA compliance will provide invaluable guidance throughout the development process and align with the latest regulatory updates. This will save your time, mitigate risks, and help avoid costly violations.
Audit partners and providers (BAA agreements)
HIPAA-compliant app development often involves third-party services, and any vendor that handles PHI must sign a Business Associate Agreement (BAA). Managing these agreements can be time-consuming, but skipping or using outdated ones puts your data at serious risk.
To stay protected, you must sign a current BAA with every vendor who has access to PHI. And review and update agreements regularly, especially when laws or best practices change.This will help you avoid data leaks and remain compliant.
Regular risks assessment
HIPAA requires you and your partners to regularly review how you handle, store, and share protected health information (PHI). These risk assessments help identify security gaps early on and avoid data breaches. Skipping or delaying risk assessments can put your organization at risk of cyberattacks and HIPAA violations.
To avoid this, you must regularly conduct a full risk assessment, especially after major system changes. Review all systems, workflows, and third-party vendors that handle PHI, and update your policies to improve your defenses over time.
Documentation and training
To stay HIPAA compliant, having the right tools is not enough – you also need proper documentation and a well-trained team. Each employee who handles PHI should be trained in HIPAA laws, security best practices, and how to cope with incidents. By training your team regularly, you reduce the risk of accidental breaches.
Keeping a detailed audit log is equally important. Ensure your system tracks every access to PHI and all modifications or activities. These logs will allow you to quickly detect and prevent suspicious behavior and prove compliance during audits. Investing in training staff and processes today – protects your patients and your organization tomorrow.
Backup and secure data disposal
HIPAA requires that you and your partners have a disaster recovery plan in place. Encrypt backups during transfer and storage and store them in secure environments. Also, test your backups to ensure data can be quickly and fully recovered when needed.
When PHI is no longer needed, it must be securely deleted using tools that meet industry standards like NIST SP 800-88. Don’t overlook devices like printers, USB drives, or employee laptops before disposal or reuse.
Cost of developing a HIPAA-compliant application
The cost of developing a HIPAA-compliant application can range from $60,000 to +$300,000 and depends on multiple factors, like the app’s complexity, timeline, developers’ location, expertise, and security level needed. Partnering with an experienced HIPAA-compliant mobile app development company will help you keep your budget under control and stay compliant.
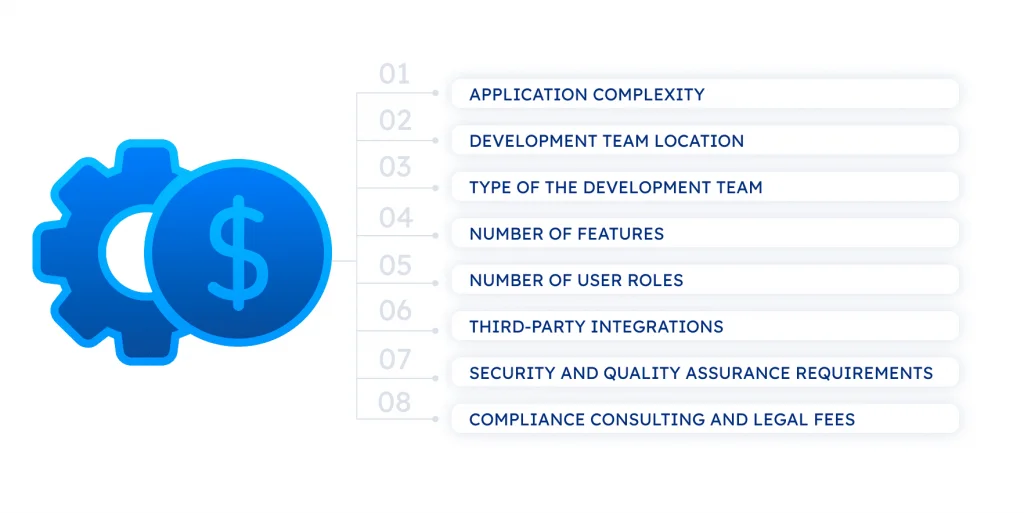
Core factors influencing the total cost a HIPAA-compliant app are:
Let’s consider each of them in-depth.
Application complexity
The cost of developing a HIPAA-compliant application depends heavily on its complexity. The more functionality an app has, the more value it will bring to its users and healthcare providers, but it will also raise development expenses. For example:
- Basic app: from $50,000 to $100,000 over 3 to 5 months with limited features and user interactions.
- Mid-level app: from $100,000 to $300,000 over 6 to 9 months with advanced features.
- Complex app: from $300,000 to $500,000+ over 10 to 13 months with multiple-platform support and advanced features.
Each additional feature adds development time and security complexity. This is why healthcare applications are among the most expensive to build.
When planning your app, you’ll also need to choose an iOS, Android, or hybrid platform. Hybrid HIPAA compliance application development is more cost-effective than separate iOS and Android ones. So select the right platform based on your budget and target audience.
Development team location
The cost of HIPAA development depends on the location of the development team. When choosing between offshore and nearshore companies, it’s important to consider both cost and experience. If you decide to outsource to a low-cost region, check its experience with healthcare and HIPAA compliance to avoid security risks and legal issues. Below are the hourly rates of developers by location:
- North America (USA, Canada): $100 – $250\hour
- Western Europe (UK, Germany): $80 – $200\hour
- Eastern Europe (Poland, Romania): $40 – $80\hour
The balance of cost, expertise in healthcare, and HIPAA compliance experience are key when selecting the right development team.
Type of the development team
Besides location, you need to select the types of developers for your HIPAA-compliant app. You can choose from in-house developers, freelancers, and development agencies.
Hiring an in-house team is a great choice if you have an unlimited budget and want to retain full control over the project and security. However, it comes with high salaries, training, and equipment costs, especially if they lack HIPAA expertise. The average price of in-house developers is $80,000 to $150,000\year.
Freelancers are a more affordable choice, allowing you to hire specialists for specific project tasks. But managing multiple freelancers can be challenging, and there’s a higher risk of missing HIPAA compliance. Freelancers are suited for short-term projects with clear scope and the ability to manage external ones. The average cost of a freelancer is $50 – $150\hour.
A development agency is a perfect option for balancing costs, healthcare expertise, and fast delivery. They offer access to skilled teams with experience in HIPAA compliance and a proven process for managing it. With a large pool of specialists and resources, they ensure end-to-end healthcare services and fast project delivery, like SoftTeco.
These agencies can be more expensive. However, you won’t have to worry about privacy regulations. The average cost of a developer from development agencies is $75 – $250\hour.
Number of features
As mentioned earlier, the number of features in the app directly impacts its cost. Each additional feature increases app complexity, requiring more time and resources, which increases overall costs. But there are basic features that each HIPAA-compliant app must include:
- For access controls: authentication and authorization, role-based access controls (RBAC), multi-factor authentication
- For data security: encryption, data anonymization, data integrity.
- For audit controls: audit trails, logging, and monitoring tools.
If you want to add advanced features for better functionality and security, you can consider secure messaging, emergency access, and biometric recognition. The cost of features can vary widely, typically ranging from $5,000 to $50,000 per feature.
Number of user roles
The more user roles, such as patient, admin, and doctor, the more complex the app will be. This is because each role requires specific permissions, interfaces, and features. Apart from that, different roles may need varying t levels of authentication, such as multi-factor authentication (MFA) or single sign-on (SSO). It increases security risk by requiring more stringent security protocols and adds to design and development costs.
Hence, it is recommended to carefully determine the number and scope of user roles to balance functionality and cost while meeting HIPAA standards. The estimated cost per user role ranges from $5,000 to $30,000.
Third-party integrations
Third-party integrations, such as cloud services, EHRs, or IoT – is a great option to extend your app functionality. But integrations with external systems can also pose additional security risks, which requires additional testing steps. Hence, every integration must support secure data exchange and comply with HIPAA regulations. To achieve this, you will likely spend a lot of development time and costs.
It is recommended to integrate only those ones that are the most essential for your app. The approximate cost of integrating third-party services ranges from $10,000 to $50,000.
Security and quality assurance requirements
Often, security and quality assurance costs make up a big chunk of the cost of an app. As HIPAA regulations impose strict security and privacy standards, the app must meet them. Essential testing includes security testing, compliance testing, performance testing, penetration testing, and functionality testing.
Basic security measures cost a few thousand dollars. More advanced measures such as vulnerability scanning and continuous monitoring will increase costs. Hiring developers with HIPAA expertise or working with third-party security vendors can also increase expenses. On average, security services may add $20,000 to $50,000 to the overall app development budget, based on the level of complexity and security required.
Compliance consulting and legal fees
Compliance consulting and legal fees are crucial for ensuring an app meets regulations like HIPAA. Consulting experts help with audits, policy reviews, and advising on compliance, while legal fees cover contracts, privacy policies, and other documentation.
These services can cost around $5,000 and $30,000, depending on the ongoing support needed.
Common myths about HIPAA compliance
Below we look at common myths related to HIPAA during app creation that you should be aware of and dispel them:
Myth 1
Every healthcare app must be HIPAA-compliant. False.
Why: Not all healthcare apps are required to comply with HIPAA. HIPAA is only necessary when the app deals with protected health information (PHI) for a covered entity (such as a healthcare provider) or serves as a business associate (BA) for them.
For example, a fitness tracker that stores step counts for personal use isn’t subject to HIPAA. But an app that shares patient data with a doctor or hospital likely is. To better understand it for your app, evaluate its features and data handling practices to determine if HIPAA applies to them, or get a consultation from compliance experts.
Myth 2
Cloud services automatically make an app HIPAA-compliant. This is false.
Why: Using a HIPAA-compliant cloud service provider does not automatically make your application compliant. Compliance depends on how you configure and use the services. Even if your vendor offers a HIPAA-compliant infrastructure, you need to make sure it is:
- Having a Business Associate Agreement (BAA) in place
- Data is properly encrypted
- Access is restricted and logged
- Complying with HIPAA privacy and security rules
Cloud providers simply offer tools. Your responsibility is to use them in a HIPAA-compliant way.
Myth 3
Encryption alone guarantees HIPAA compliance. This is false.
Why: While encryption is an important safeguard, it’s only one part of HIPAA compliance. The HIPAA Security Rule outlines a broad set of administrative, physical, and technical safeguards. In a nutshell, encryption is major but not enough on its own. To be fully compliant, organizations must also conduct risk assessments, implement access controls and audit logs, etc.
Myth 4
HIPAA compliance is a one-time process. This is false and false again.
Why: HIPAA compliance is an ongoing process, not a task that can be accomplished once. As technology changes, threats evolve, and organizations grow so your HIPAA compliance procedure must adapt accordingly. HIPAA regulations require ongoing monitoring, regular risk assessments, and updates to ensure your security and privacy measures stay effective and up to date.
Myth 5
HIPAA compliance is too expensive. False.
Why: Of course, HIPAA compliance requires some investment, but it doesn’t have to be expensive. In most cases, HIPAA compliance can be achieved with a varied budget, especially with a consistent and strategic approach. Many of the measures required by HIPAA are based on already existing security best practices. For example, сloud providers offer built-in security mechanisms, such as encryption, log auditing, or access control.
Remember, the implementation costs are much lower than the potential fines (up to $50,000 per year for each violation) not to mention the financial and reputational damage.
Conclusion
HIPAA compliance application development is a complex process that involves careful planning, investment, and regular review. By following the strict rules set by HIPAA, using secure technologies and setting up strong security measures, you can create an app that meets legal standards and builds user trust. As mobile health solutions continue to grow, knowing how to build a HIPAA-compliant app is key for the future growth.
If you need professional guidance with HIPAA compliance, contact SoftTeco – we will advise you on how to make an app HIPAA-compliant so you can focus on your business without worrying about legal risks.
Expert Opinion
From my experience leading healthcare software projects for clients across the U.S. and Europe, I can confirm that HIPAA compliance is not just a checklist – it’s a culture of security, transparency, and continuous vigilance.
We’ve seen cases where vendors assumed compliance based on infrastructure alone, only to discover gaps during audits. A compliant cloud setup is only as good as its configuration and the operational controls around it.
Security testing, logging, and monitoring tools have proven indispensable in our own HIPAA projects. But what often matters most it’s how well a company follows HIPAA policies, trains employees, and regularly checks for compliance. HIPAA is a continuous process so aligning technology with the company’s processes is key to long-term success.



Comments