Table of Contents
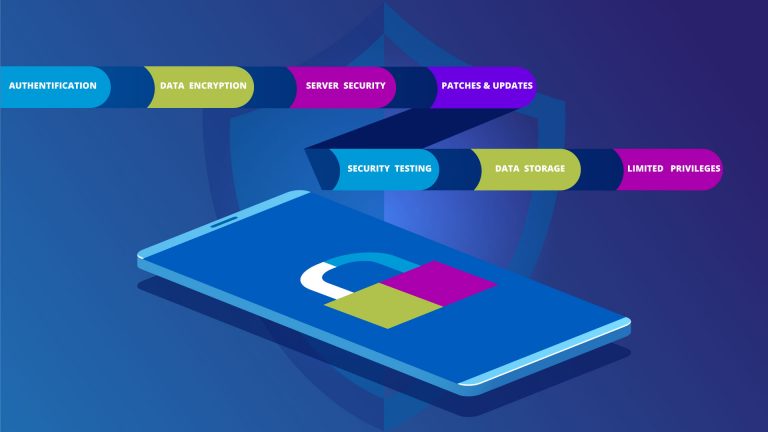
The Main Security Issues in the Mobile App Development
The advancement of technology allows software providers to create more secure and robust solutions but, at the same time, it also provides opportunities to design more advanced tools for hacking.
The issues of security breaches and data leaks are of utmost concern for any software development provider. Last year, the average cost of a data breach was $3.8 million. The same figures were reached by the third quarter of 2019 and are expected to climb up to $6.5 million by the end of the year.
No company would like to face such costs, hence, it is vital to follow certain security practices to prevent any hacker attacks. It is especially important for mobile app developers since mobile applications tend to be the most vulnerable. SoftTeco collected the main security issues to keep in mind when developing a mobile application.
Provide high-level authentication
The process of authorizing a mobile app user can be one of the primary points of attack. There are numerous ways how hackers can bypass the app authentication, including the brute force attack and “Fake Finger” to bypass the biometric authentication.
Considering the advanced hacker tools, no one can guarantee 100% security of an app – but a higher authentication level implies higher chances for retaining the data safe and protected.
The basic authentication form that most mobile apps have is the password, either a 4- or 6-digit one. To enhance the authentication, you can implement the following additional methods:
- Biometric authentication (face or fingerprint scan)
- Confirmation via the SMS
- A certain number of login attempts
- Obligatory strong password
It is critical to store passwords and PIN codes either encrypted or hashed. As well, never store sensitive data in the source code as it increases the risk of a hacker attack. The best option would be to store the passwords on the server. However, in the case of biometric authentication, the PIN is stored in the device. To secure it, store such data only in the verified local storage: Keychain for iOS and Keystore for Android apps.
Make sure the data is encrypted
If the sensitive data is stored in a simple text format, your app might be in huge, huge trouble.
Data encryption is an absolute must for any software product that stores and manages sensitive data, like users’ passwords. There are certain rules to follow when encrypting your data, as OWASP states. But before getting down to them, one should first know about the different cryptographic algorithms:
- Symmetric: implies that there is only one key for data encryption and decryption,
- Asymmetric: there are two different keys, one for data encryption and the other for its decryption,
- Hashes: make it highly difficult (and even impossible) to generate the original input (i.e. a password).
Each of these algorithms has certain standards to follow in order to protect the data from any potential attacks. For example, different key and hash sizes are required for different algorithms – learn more on the official OWASP page.
Verify third-party code
Depending on the app’s complexity and purpose, the process of its development can take quite a while. To save some time, engineers often use available tools like libraries or frameworks to speed up the process. And this is a danger zone.
Some third-party tools can contain malware, intended to attack your app. Or they can simply be written in a poor and vulnerable code, prone to the attacks. To avoid risks, either do not use third-party tools at all or thoroughly test and verify them.
Enhance the server-side security
The primary method of securing the server-side of your mobile app is to use the SSL protocols, preferably recommended by OWASP. The Security Socket Layer (SSL) certificate secures the data in a number of steps known as “SSL Handshake”:
- Exchange of certain information between the SSL certificate and the server
- Authentication of the server and the client-side
- Exchange of the encryption keys
As you see, SSL can significantly secure your server. The sites that have SSL certificate will have HTTPS instead of HTTP.
However, SSL does not guarantee 100% security either. To optimize it even more, you can use certificate pinning. That means the certificate is embedded in the code of the app, making the app independent of the certificate store of its OS. This way, you can prevent MITM attacks.
Remember about updates and security patches
Updates are not just some random recommendations from the developers’ community. They are actually a powerful aid in battling the hackers’ attacks and securing your app.
Both iOS and Android provide developers with regular security updates and patches, aimed to fix the bugs and secure the app. Such updates may provide safer backup, enhanced network security, or prevention of asses to your sensors for the malware and are overall aimed at eliminating the vulnerabilities of the software products.
While updates and patches will not protect the app from major forms of attack, they serve as an additional line of defense.
Perform thorough and regular security testing
360-degree testing is an absolute must when it comes to the development of any software product and secure testing is the precautionary measure that will keep your application safe from hacker attacks.
When testing an app for any security breaches, keep an eye on the main areas:
- Authentication (including password testing, stateful authentication, etc.)
- Session management and timeout (it is recommended to limit the session duration and is obligatory to create a new session every time the old one expires)
- Logout (shows whether the logout leads to the session termination)
- Login activity (whether the app notifies the user about it)
- Security of network communication (testing for different kinds of attack)
- Data encryption (verification of the correct data encryption)
- Code quality (whether it’s strong enough and does not have any breaches)
- Data storage (must be securely stored)
Because mobile applications are the most vulnerable to hacker attacks, it is important to regularly perform security testing and implement the latest security updates.
Secure the data storage
Did you know that insecure data storage is the most common issue for both iOS and Android mobile apps? With 76% of the apps storing the data in a non-secure manner, these apps are at a huge risk of the data leak.
The mobile device stores a great amount of sensitive data, like geolocation or financial data. The leak of such data may lead to serious consequences: identity theft, fraud, and similar issues. To prevent them and enhance the security of your application, check for the following:
- The way the app’s OS caches the data, buffers, logging,
- The way HTML5 stores data
- The way data is sent to the third parties
- The way sensitive data is masked in the background.
OWASP covers insecure data storage in full and provides useful recommendations on the best practices.
Enable limited privileges
It is common practice to have different levels of access for different user roles in order to keep sensitive information secure. In terms of app development, you should check whether the app has a limited number of users that can access the admin function controls.
If privileged information can be easily accessed by a big number of users or even by non-authorized users, that will lead to big problems. Thus, double-check the access configurations on a regular basis and perform testing to ensure the access is available for authorized users only.
Summary
Depending on the app’s complexity and intended usage, you will most probably need a unique combination of techniques that will help secure the data and your app. However, the methods mentioned above can serve as a solid base, aimed at securing the app and preventing the majority of hacker attacks. Any mobile developer should consider these practices during the app development and deploy them by default.


Comments